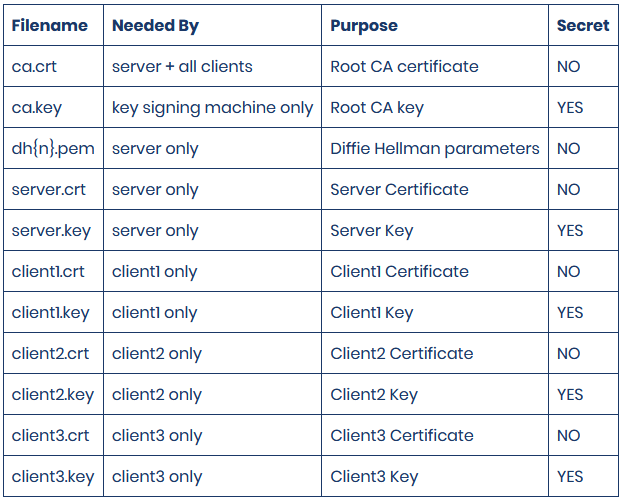
The original article I wrote a couple years ago has held up pretty well but now that OpenVPN 2.5 has shipped with EasyRSA v3 there will have to be some changes. Additionally the latest Ubiquiti Edgerouter 2.0.9 firmware should be used.
This article is complete in itself but the original article has more theory and discussion that still applies. If this isn’t making sense then maybe the other article will help out. Also the OpenVPN community has some excellent resources, the original HOWTO article has seen some work there, and EasyRSA v3 has it’s own simplified page.
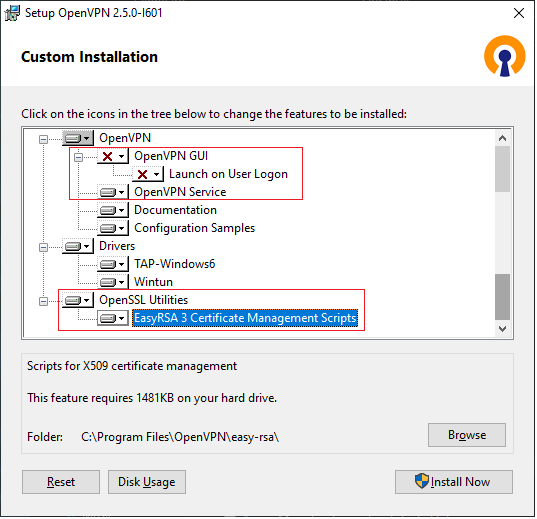
The OpenVPN Community edition installer is just a tiny bit different, you will need to configure it so you can get the tools you need. You don’t need the GUI, you do need the service and EasyRSA scripts;
OpenVPN server config
No really big changes here, in fact your old server config will drop right in to 2.5. Two small changes:
First off the ciphers will throw an error in your server log as 2.5+ handles ciphers a little different so;
data-ciphers-fallback AES-256-CBC
Also the Ubiquiti Edgerouter now supports a compatible compression;
compress lz4-v2
push "compress lz4-v2"
Do not use compression, see this article explaining it.
The folder where these files go has changed, place the server.ovpn file and ccd folder in C:\Program Files\OpenVPN\config-auto
Complete server.ovpn here but take a moment to think about network planning too:
### For minimum versions OpenVPN 2.5.0 / EasyRSA 3 / Edgerouter 2.0.9
### This file compatible with topology SUBNET
### Remember to edit LAN addressing for server routing below, and client addressing in CCD files
### Server VPN IP is 10.8.0.1, bind BMS to that IP.
### Set OpenVPN service to automatic startup (no delay) so that the IP will be there when BMS asks.
### Set BMS to delayed start.
### Connection info
proto tcp4-server
port 1194
mode server
keepalive 10 120
### encryption info EasyRSA v3
tls-server
remote-cert-eku "TLS Web Client Authentication"
data-ciphers-fallback AES-256-GCM
ca "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\ca.crt"
cert "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\issued\\server.crt"
key "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\private\\server.key"
dh "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\dh.pem"
### authentication
tls-auth "C:\\Program Files\\OpenVPN\\easy-rsa\\pki\\ta.key" 0 # This file is secret
# Enable compression on the VPN link and push the
# option to the client (v2.4+ only)
;compress lz4-v2
;push "compress lz4-v2"
# compression disabled, anti voracle attack
# https://openvpn.net/security-advisory/the-voracle-attack-vulnerability/
### Network
# FYI; VPN DHCP server is on 10.8.0.254
# route gateway is 10.8.0.2
# server is on 10.8.0.1
# always avoid these addresses when addressing clients via CCD
dev tun
topology "subnet"
push "topology subnet"
server 10.8.0.0 255.255.255.0
# Push routes to connecting clients, they need to know how to route to other LANs
push "route 10.105.101.0 255.255.255.0"
;push "route 10.105.102.0 255.255.255.0"
;push "route 10.105.103.0 255.255.255.0"
;push "route 10.105.104.0 255.255.255.0"
;push "route 10.105.105.0 255.255.255.0"
;push "route 10.105.106.0 255.255.255.0"
;push "route 10.105.107.0 255.255.255.0"
# Allow LAN routing between clients
client-to-client
# Allow the server to route traffic to client LANs
route 10.105.101.0 255.255.255.0
;route 10.105.102.0 255.255.255.0
;route 10.105.103.0 255.255.255.0
;route 10.105.104.0 255.255.255.0
;route 10.105.105.0 255.255.255.0
;route 10.105.106.0 255.255.255.0
;route 10.105.107.0 255.255.255.0
# ovpn server pushes config info to clients from files in ccd dir.
# Matches are based on CN in connecting key, so CN in key must match file name exactly.
# Static VPN addressing and Client LAN routing is controlled in these files.
# client configuration directory (home is config dir, so rel path ok here)
;client-config-dir ccd
client-config-dir "C:\\Program Files\\OpenVPN\\config-auto\\ccd\\"
### Logging
# OpenVPN log goes to C:\Program Files\OpenVPN\log\* whatever this ovpn file is named
# 0 is silent, except for fatal errors
# 3 default?
# 4 is reasonable for general usage
# 5 and 6 can help to debug connection problems
# 9 is extremely verbose
verb 3
# read this to see what clients are connected
status "C:\\Program Files\\OpenVPN\\log\\openvpn-status.log"The CCD files themselves are unchanged from previous versions. Remember the CCD file name must match the client name for these to apply to that client. In this case this is file name client1 and you will need one file per connecting client. Change iroute line to match subnet of the remote router LAN, and the ifconfig-push is just giving it a static client IP reservation so those need to be uniquie.
iroute 10.105.101.0 255.255.255.0
ifconfig-push 10.8.0.11 255.255.255.0So far not a big change from earlier versions, that ends here. EasyRSA v3 is a big departure and it’s all for the better IMO. I’m going to suggest at a minimum you put this vars file in C:\Program Files\OpenVPN\easy-rsa\vars (no file extension).
# see vars.example for settings usage
# This file belongs in; C:\Program Files\OpenVPN\easy-rsa
# Organization info, remember to edit the OU for server name
set_var EASYRSA_REQ_COUNTRY "US"
set_var EASYRSA_REQ_PROVINCE "NY"
set_var EASYRSA_REQ_CITY "NewYork"
set_var EASYRSA_REQ_ORG "BMSvendor"
set_var EASYRSA_REQ_EMAIL "it@example.com"
set_var EASYRSA_REQ_OU "server#5"
# In how many days should the root CA key expire; 20 years
set_var EASYRSA_CA_EXPIRE 7300
# In how many days should certificates expire; 20 years
set_var EASYRSA_CERT_EXPIRE 7300
# How many days before its expiration date a certificate is allowed to be renewed; whenever
set_var EASYRSA_CERT_RENEW 7300
# 3.0.8 path bug workaround; https://github.com/OpenVPN/easy-rsa/issues/412
# you must create C:\Temp
set_var EASYRSA_TEMP_DIR "C:/Temp"Your organization information should be changed to match your org, and I’d suggest the OU match the server name. 20 year keys by default are pretty easy to deal with, remember we have complete control of key revocation so no need for short lived keys. Lastly the current EasyRSA v3.0.8 has a little bug we need to work around, unfortunately still there at the time of this writing but hopefully this can be dropped soon. Make sure you create folder C:\Temp
Now we are ready to actually create the keys we need. You will notice that the amount of info you need to enter to complete these is MUCH less, plus the less paranoid DH size is a little more realistic and with these two things this process is a LOT faster. With Administrative command prompt at C:\Program Files\OpenVPN\ run EasyRSA-Start.bat. This will get you into a shell similar to a linux CLI. This is a list of commands you need to run;
easyrsa init-pki easyrsa build-ca -SAVE the ca passphrase you make up!!
easyrsa build-server-full server nopass
easyrsa build-client-full client1 nopass
easyrsa build-client-full client2 nopass
easyrsa build-client-full client3 nopass
easyrsa build-client-full client4 nopass
easyrsa build-client-full client5 nopass
easyrsa build-client-full client6 nopass
easyrsa gen-dh Should not take that long with a 2048 bit dh
cd pki
openvpn --genkey secret ta.keyA side note on private key handling; As you can see we are creating these keys on the actual server as I've written it. A much better way to handle these keys would be to have your RSAv3 infrastructure on a computer dedicated to that role and only the keys necessary for server and clients leave it. Next level would be to do the signing procedure the scrips suggest so that the private keys for the clients aren't even in your infrastructure. This requires installing these scripts on the Edgerouter, not something I wanted to attempt. The reason I'm not doing these things is realistically if an adversary is in a position to take these keys off of the server, then the game is already over.
That’s it, Start the “OpenVPNService” service and set it to Automatic start (no delay).
Observe log file for errors C:\Program Files\OpenVPN\log\server.log
After you have configured some clients you can observe the connection log to see what client is connected. C:\Program Files\OpenVPN\log\openvpn-status.log
Edgerouter as VPN client
Setting up the Ubiquiti Edgerouter is nearly identical to the previous article. Router defaults, new out of the box or after reset are; 192.168.1.1, open a web page to that address User: ubnt Pass: ubnt. Connect to eth0 on the EdgeRouter with a similar IP. Ubiquiti used to put this on instructions included in the box, no idea why they stopped doing that.
Upgrade the firmware to the lastest Ubiquiti has, 2.0.9 as of this writing. Make sure you update the bootloader too. The first time you SSH into the Edgerouter it will remind you in easy to follow CLI, it only takes a second and one command to complete.
Start configuring the router with BASIC setup wizard in the web page “Wizards” in far right GUI menu, select “basic” wizard. Set LAN subnet same as required for IP scheme you previously worked out. Set user/pass and save that somewhere. Save all that and reboot the router, move your cable and change your IP to connect to the LAN. The WAN port can also be connected to the internet now.
OpenVPN client config files are very similar to the old article. I’m going to suggest you keep a copy of this file on the server too. This file is named client1.ovpn and for client two you just need to copy it, rename it client2.ovpn and change the key name numbers to match.
# This file compatible with topology SUBNET
# Intended for Ubiquiti ERX or similar
# Edit this file name to keep things straight, retain on server in folder: C:\Program Files\OpenVPN\easy-rsa\client-configs
# VPN type
client
# Connection setup
proto tcp-client
remote demo.example.com 1194
nobind
# Encryption
cipher AES-256-GCM
tls-client
remote-cert-eku "TLS Web Server Authentication"
# -Windows roadwarrior
;ca "C:\\Program Files\\OpenVPN\\config\\ca.crt"
;cert "C:\\Program Files\\OpenVPN\\config\\client1.crt"
;key "C:\\Program Files\\OpenVPN\\config\\client1.key"
# -Ubiquiti EdgeRouter
ca /config/auth/ca.crt
cert /config/auth/client1.crt
key /config/auth/client1.key
# Authentication
tls-auth /config/auth/ta.key 1
# Compression
;compress lz4-v2
# compression disabled, anti voracle attack
# https://openvpn.net/security-advisory/the-voracle-attack-vulnerability/
# Network setup
dev tun
# Logging level
verb 3You need that file above and the ca.crt, client#.crt, client#.key, ta.key files. They come from the server in directory: C:\Program Files\OpenVPN\easy-rsa\pki inside the issued and private folders.
Push those files to the Edgerouter using a sftp file client like Filezilla or WinSCP. They all need to go in folder /config/auth.
Interesting anecdote; While I was doing some testing back in 2016 for the first article I was concerned after finding these VPN key files would remain on the Edgerouter after a factory reset, potentially giving an adversary access to them using the default login credentials. Further prompting on UI forums this year also went nowhere. I went through all the hoops to create a HackerOne account and did a write up on this problem for HackerOne and UI. The bug was accepted, I was given a $100 reward, and the fix is present in Edgerouter firmwares 2.0.9 and higher. I now have a much greater understanding of what security researchers must deal with as it wasn't a short process even after I went through official channels.
Now you need to SSH into the Edgerouter. There’s a console built into the Edgerouter web page, and these days windows 10 now has a SSH client, but I still use putty.
configure (this gets you to the config environment in the router. Shell=$ prompt, Config=# prompt)
set interfaces openvpn vtun0 config-file /config/auth/client#.ovpn (pay attention to file name)
commit (were there any errors? If no:)
save
exit (will exit the config environment and drop back to shell $)To view VPN status in SSH shell prompt use command; show interfaces openvpn detail That will return nothing if tunnel is not up. If that happens view log with egrep openvpn /var/log/messages To see the last 50 lines of the entire log tail -50 /var/log/messages Also in the VPN server read file C:\Program Files\OpenVPN\log\clients.log
Security; LAN facing firewall
One of the top reasons I like the Edgerouter is the firewall in it is very powerful. The original article covered this really well. I’ve been doing these firewall rules before the Edgerouter leaves the office but I can see where some might want to leave that until the site is commissioned. The ports I’ve defined are for a Automated Logic WebCTRL system and if your BMS is different you will need to research the ports in use and allow those.
Physical security is also important, make sure the Edgerouter is locked up so it isn’t stolen. Anyone that steals it and gives it internet access can get remote access to your BMS network at whatever level you enabled on the LAN firewall.